Askedam Deception
Easily configure decoy files, users, hosts, and networks to expose malicious actors who have gained access to your environment.
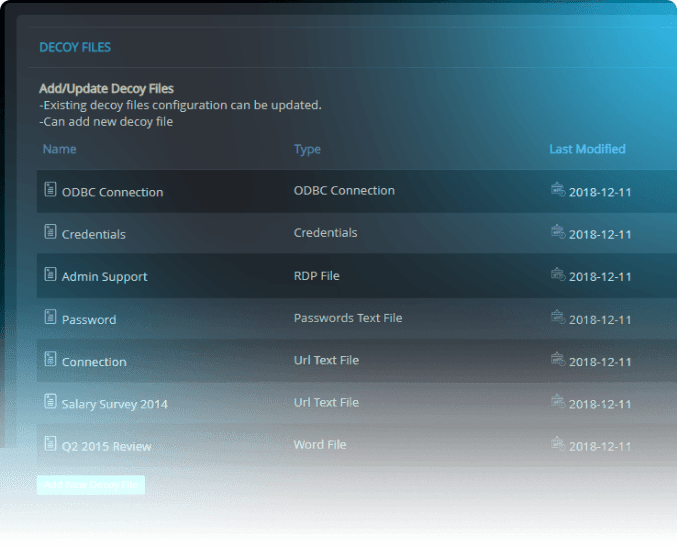
Use off-the-shelf decoys or craft your own
Askedam deception supports various types of decoys, to detect threats in various stages of the attack’s lifecycle: data files, credentials and network connections.
In each type, the consumption action triggers the alert – login attempt with a decoy password, connection attempt with RDP or URL and opening a data file.
Detect attacks at different stages
Detect attacks at the credential theft stage with decoy passwords
Passwords are extremely valuable to attackers attempting to expand their foothold within a compromised environment. Askedam crafts and plants text files containing false passwords along attackers’ potential routes. Any attempt to log in with these passwords triggers an alert.
Detect attacks at the lateral movement stage with decoy connections
When seeking to expand compromise across the environment to access organizational resources, internal network shares and RDP connections are extremely attractive. Askedam’s decoy connections enable the reliable detection of attackers during the hard –to-detect lateral movement stage.
Detect attacks at the data exfiltration stage with decoy data files
The attacker’s top object is to get hold of sensitive data – IP, PII, business plans, etc. Askedam crafts and plants decoy data files and links – similar to what attackers would seek in the target organization – and plants them across endpoints and servers in the environment.
Detect attacks at the data exfilatration stage with decoy data files
When an attacker opens a decoy data file at its premise, an alert is triggered and the file sends Askedam the malicious IP address at which it resides.
