Askedam User Behavior Analytics Rules (UBA)
Askedam UBA security layer monitors user behavior to spot and isolate compromised accounts
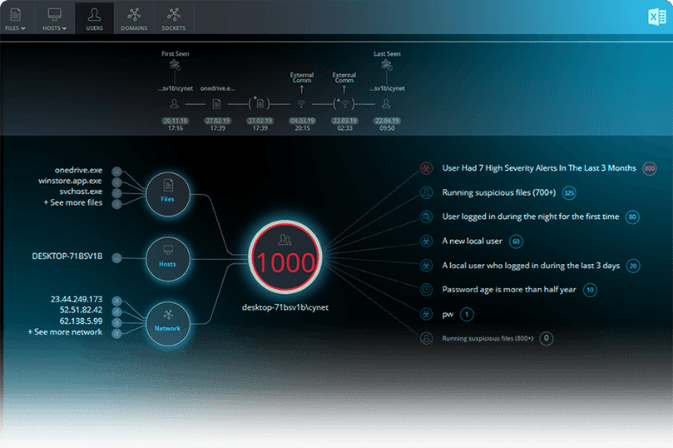
Customize baseline user behavior
Use associate information, like role, group, geolocation, working hours and more to define normal behavioral patterns, then automatically detect suspicious activity, such as first-time and off-hour logins.
Get real-time activity context
Askedam continuously correlates user activities against other events — such as endpoints, files and external network locations — to provide holistic information to determine real-time risk levels.
Automate alerts and remediation
Receive alerts whenever Askedam detects suspicious activity. You can also automatically disable compromised accounts or review activity context to take necessary action.
Verify users with two-factor authentication
Askedam continuously correlates user activities against other events — such as endpoints, files and external network locations — to provide holistic information to determine real-time risk levels.
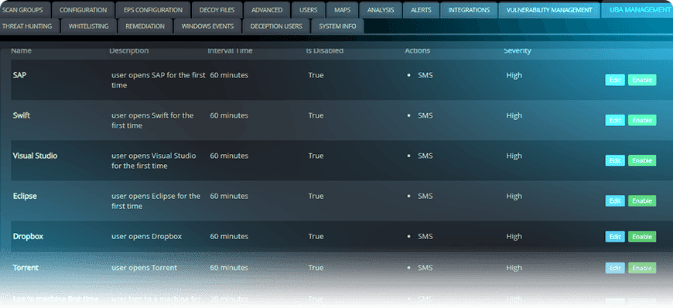
User behavior analytics: common scenarios
Anomalous Login
User is logged in to his laptop and logs in to a sensitive database.
New VPN Connection
User remotely logs in to a file server via VPN for the first time.
Multiple Concurrent Connections
User is logged in to multiple resources within a short timeframe.
Off Hours SAAS Login
User that typically works on an on-prem desktop logs in remotely to the organization’s Dropbox.



