Correlate Signals Into Actionable Incidents
Achieve SIEM-like capabilities included out-of-the-box in Askedam AutoXDR platform.
Combine threat signals to uncover attacks using a single, easy-to-use platform.

Event Correlation
Collect and correlate alert and activity data from Askedam Protector™ and other sources into actionable incidents with Next Generation SIEM capabilities.
Centralized Log Management (CLM)
Collect and integrate critical log data needed for threat analysis using powerful query language along with intuitive graphics and dashboards.
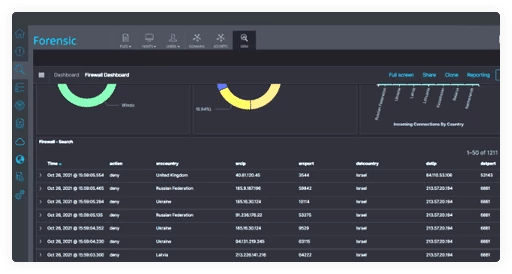
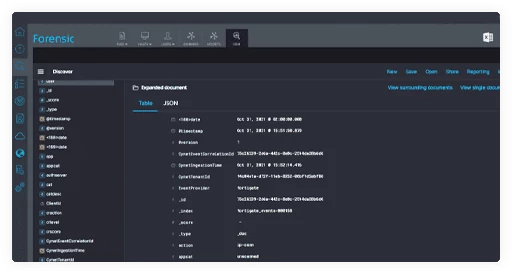
Forensics
Investigate threats and conduct threat hunting with instant access to forensic artifacts collected from Askedam agents, logs, and other system resources using powerful search and visualization tools.
Consolidate
Investigate alerts, remediate threats, orchestrate, and automate incident response workflows across your environment, all from a single pane of glass
Intelligent correlation and Centralized Log Management
Make Threat Detection More Accurate
Askedam Correlator™ analyzes all threat signals to provide full context to all alerts, so even the stealthiest attacks are detected and false positive detections are dramatically reduced.
Leverage Log Data
Askedam Centralized Log Management (CLM) provides intuitive query and visualization tools to quickly analyze log data and uncover threats across your environment
Improve Your Time to Response
Askedam Correlator provides immediate visibility into stealthy attacks by combining signals from endpoints, networks, users and decoy beacons
Reduce Cost and Complexity
Avoid the costly and resource-intensive implementation and support of a complicated SIEM solution – Correlator is included in Askedam AutoXDR platform
How can Askedam Correlator™ help?
- Does your organization take too long to discover and respond to threats?
- Do you suffer from imprecise threat detection?
- Does your team fully leverage log data?
- Are your security controls disjointed?



