Askedam Endpoint Detection and Response (EDR)
Askedam robust EDR security layer that continuously monitors endpoints for known and unknown threats and fully automates response workflows across the environment
Askedam EDR provides comprehensive visibility and protection across all attack vectors, fully automating response workflows across the entire environment, all backed by a 24/7 MDR service
Advanced endpoint detection techniques to prevent and detect both known and unknown threats across your environment
Full visibility across endpoint, network and users, along with deception technology, to detect stealthy attacks
Automatically launch responses that chain various investigation and remediation actions into a single flow
Askedam’s cybersecurity experts monitor your environment 24/7 to ensure that no attacks are overlooked and provide expert advice and guidance
Go beyond EDR to XDR
Askedam goes beyond traditional endpoint protection, combining telemetry from additional sources, to improve visibility, accuracy and protection across the entire attack surface.
Next-Gen Antivirus
Blocks execution of malware, exploits, fileless, Macros and ransomware
Network Detection and Response
Monitor network traffic to unveil reconnaissance, credential theft, lateral movement, and data exfiltration attempts
User Behavior Analytics
Profile the behavior of all user accounts to pinpoint anomalies that indicate an attempted compromise
Deception Technology
Plant various types of decoy files across your environment to lure attackers into revealing their presence
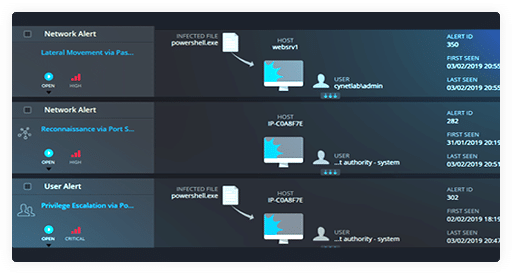
Unify incidents
Askedam automates investigations by combining related alerts into unified incidents.
End-to-end Response
Single, unified view eliminates the need to switch between solutions for investigation
Incident View
Correlate signals from multiple native detection sources into incidents to visualize and understand threat context
Automated Response
Simplify investigations with automated root cause analysis and full threat scope visualization
IOCs
Uncover Indicators of Compromise (IOCs) and anomalous behaviors

Eradicate malicious presence with automated incident response
Pre-built and custom remediation tools accelerate and optimize incident response workflows, providing a full remediation arsenal directly from the Askedam console.
Pre-built Remediation
Askedam 360 AutoXDR™ provides a pre-built remediation toolset for each entity type: file, host, network, and user. With these pre-built remediation and incident response tools, Askedam accelerates and optimizes incident response workflows, equipping security teams with a full remediation arsenal without ever needing to shift from Askedam’s console.
Automated remediation playbooks
Askedam empowers responders to accelerate their workflows by defining automated response playbooks for various attack scenarios. Any pre-set or custom remediation action can be saved as a playbook either by itself, or chained with other remediation actions. Askedam automated playbooks minimize the need for manual response actions.
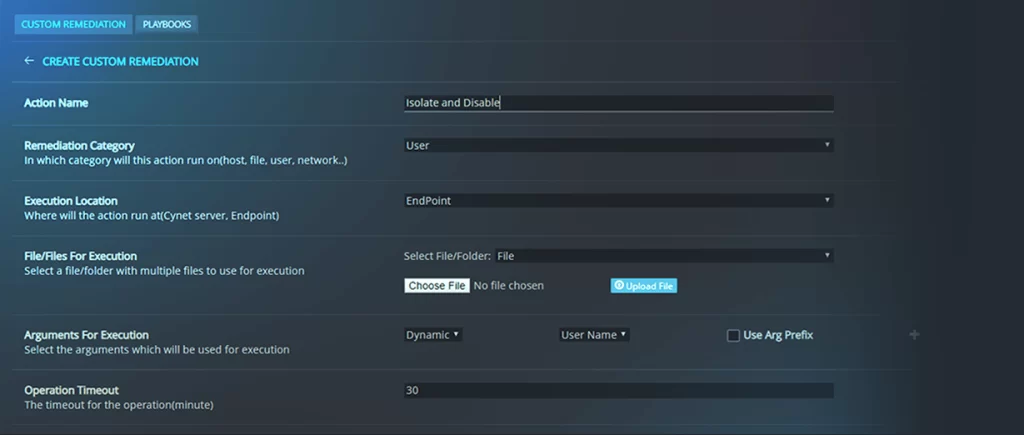
Custom Remediation
Askedam 360 AutoXDR™ pre-built remediation tools can be combined with user-created scripts that communicate with core environment components such as firewalls and active directory as part of a large-scale response orchestration workflows.
Leverage CyOps 24/7 MDR Team
CyOps, the Askedam MDR team of cybersecurity experts and researchers, is always monitoring your environment to uncover potential ransomware threats and ready to assist with response.
Implement New Detection Mechanisms
Ransomware variants discovered externally or across the Askedam client base are analyzed by CyOps analysts for specific identifiers which are implemented into Askedam detection mechanisms.
Update IoCs
Deep-dive into validated attack bits and bytes to gain the full understanding of scope and impact, providing the customer with updated IoCs.
On Demand Analysis
Customers can send suspected ransomware files to analysis directly from the Askedam 360 AutoXDR™ console and get an immediate verdict from expert CyOps analysts.
Remediation Instructions
Investigated ransomware attacks conclude with concrete guidance to the customers on what should be remediated and assistance creating customized remediation playbooks.
Threat Hunting
Proactively search for hidden threats leveraging Askedam 360 AutoXDR™ investigation tools and over 30 threat intelligence feeds.
24/7 Proactive Monitoring
Continuously monitoring your environment for ransomware and immediately contact you when incidents are detected along with specific actions that should be taken.



